-
New to Jedi Knight?
Everyone has to be the new guy at some point. If you're new to the series or one of the aspects of the game like modding or playing multiplayer, you're not alone. One thing that these games struggle with is the steep entry point and learning curve. Luckily, we have a community that would love to help you out. Check out these links to get started!
Getting Started Recommended mods Learn to mod No servers in the server list?

-
Our picks
-

-
![[WIP] Ecumenopolis Jedi Embassy](//jkhub.org/applications/core/interface/js/spacer.png)
[WIP] Ecumenopolis Jedi Embassy
Iffo posted a topic in WIPs, Teasers & Releases,
This project has been on and off for the last 18 months, and still has a long way to go but I've reached the point where I want to share a few screenshots 🙂. Targeting an end of the year release but that is very much reliant on motivation and free time aligning!
It is being created with my former RP community in mind as they still serve to inspire the design and many features of the map but a 'white label' version will be released.
Concept
A RP focused 'temple' map set on an Ecumenopolis planet. Purposefully built over a small foot print (Square footage is expensive in the city don't ya know!) but still providing essential services expected from a Jedi facility. Set atop a skyscraper and backing onto a series of repurposed warehouses and alleyways.
-
- 4 replies

Picked By
Circa, -
-

Post in JKChat A.K.A. Jedi Knight mobile application
ent posted a post in a topic,
Updated the app.
Changed:
- added minimaps in chat
- added center print message in chat
- added merging info messages into one
- added scores and game timer in chat
- added team colours highlighted in server info
- server info updates are synchronized across apps pages and widgets
- Android: replaced navigation Animations to match Material Design 3 guidelines
- Android: improved notifications to show colourful messages
- Android: fixed hanging out Widgets with always displaying the loading indicator
- iOS: added Live Activity to show connection status, players and messages count when minimized
- iOS: fixed never loading data in Widgets on iOS 18
- iOS: improved gradients animation on screen size changes
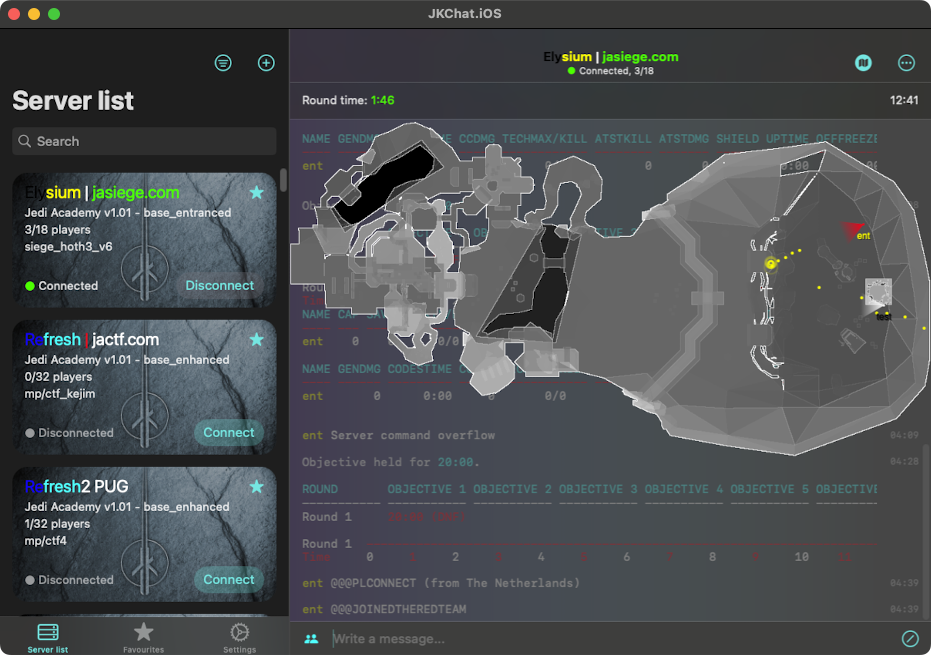
Oh no, it's a new JKChat update again with a lot of cool features.
Minimaps! The feature explains itself. But let me talk more about it. The chatting itself is fine but sometimes it feels like you are missing the game context when the in-game players start playing and chatting less. And minimaps partially solve that issue fortunately. You can see players, their names, shots, impacts, flags and players in vehicles.
Unfortunately, many game entities are only visible in a close range, but with minimaps I added some extra predefined commands to help spectating other players. Just hit the [/] button and select /follownext or /followprev to cycle through players you want to follow. An eye emoji 👁 will appear next to the spectated
Picked By
Circa, -

Holocron Challenges Mod version 2
Plasma posted a post in a topic,
Version 2 of Holocron Challenges has been released and is avaliable to download now! Without further ado let me take you through the new features and changes.
Picked By
Circa, -

Post in Kualan's Kitbash Workshop
Kualan posted a post in a topic,
A few WIP updates today -
Inspired by her recent appearance in Tales of the Underworld, I worked on revamping my old Ventress bounty hunter kitbash. Interestingly, there was already a newer version of that kitbash floating around the Internet, where someone had improved on my original with some nice retextures and some extra meshes (like the energy bow). I have included these in my own revamped version, which includes a modified Dark Disciple hair mesh and some much-needed improvements on the weights (especially in the hip/waist area). I've also upscaled several of the textures for a better overall appearance:
I've also settled on what I think will be the third and final version of Tholme:
And have started work on a pack of Jedi alien variations. I imagine this will be particularly popular with RP players. I started work on a similar pack years ago but I don't think I ever released this. I am making this one again from scratch.
(Note on the robe textures: the release version will just give them standard Hapslash textures, since the ones in the previews are sourced randomly and might include people's personal skins that I don't have permission to distribute):
Picked By
Circa,
-
-
Latest Mods
-
Popular Mods
-
Articles
-
- 0 comments
- 716 views
-
- 5 comments
- 2,670 views
-
- 2 comments
- 3,973 views
-
- 3 comments
- 3,162 views
-
- 5 comments
- 5,916 views
-
- 3 comments
- 13,391 views
-



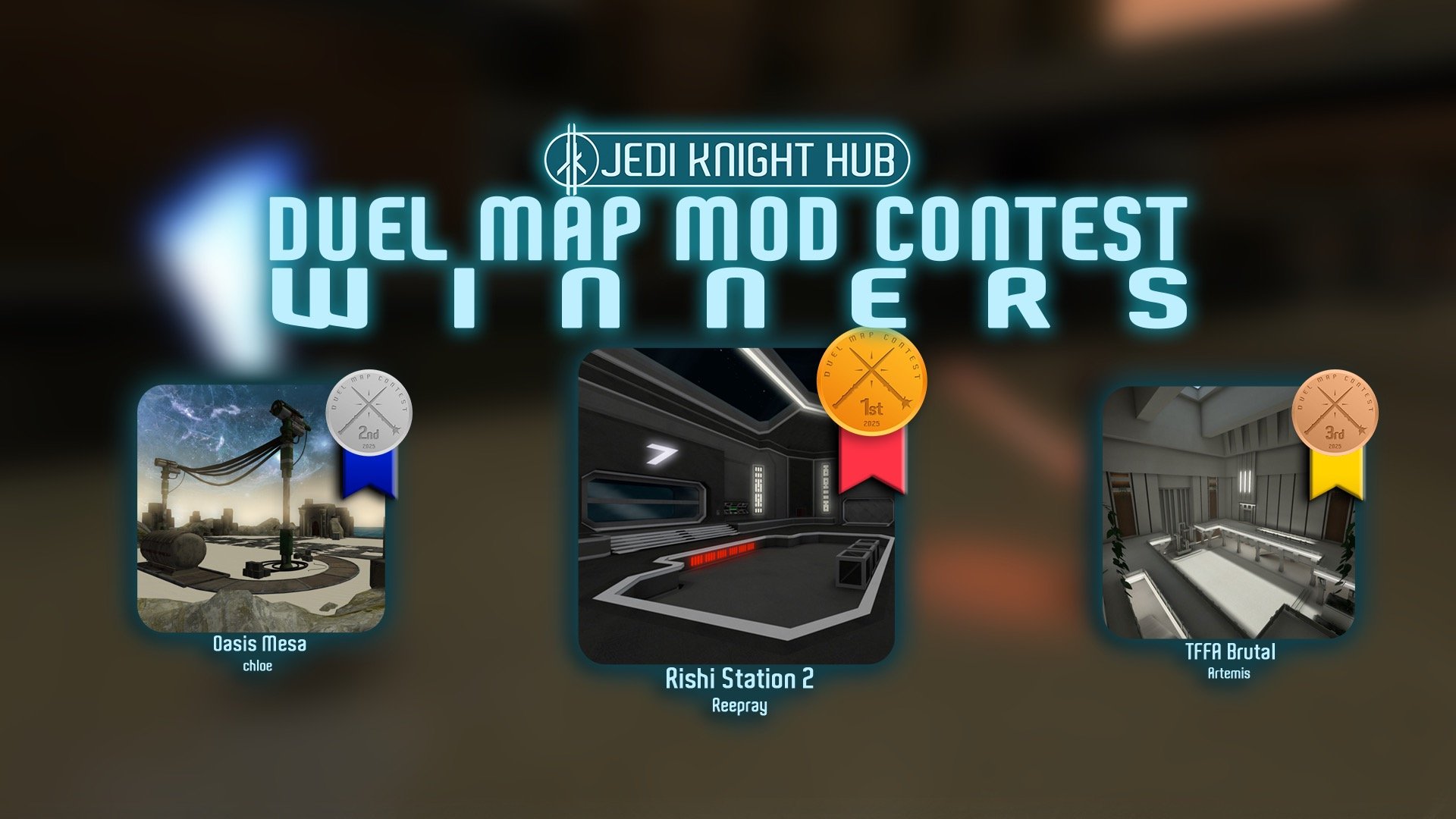
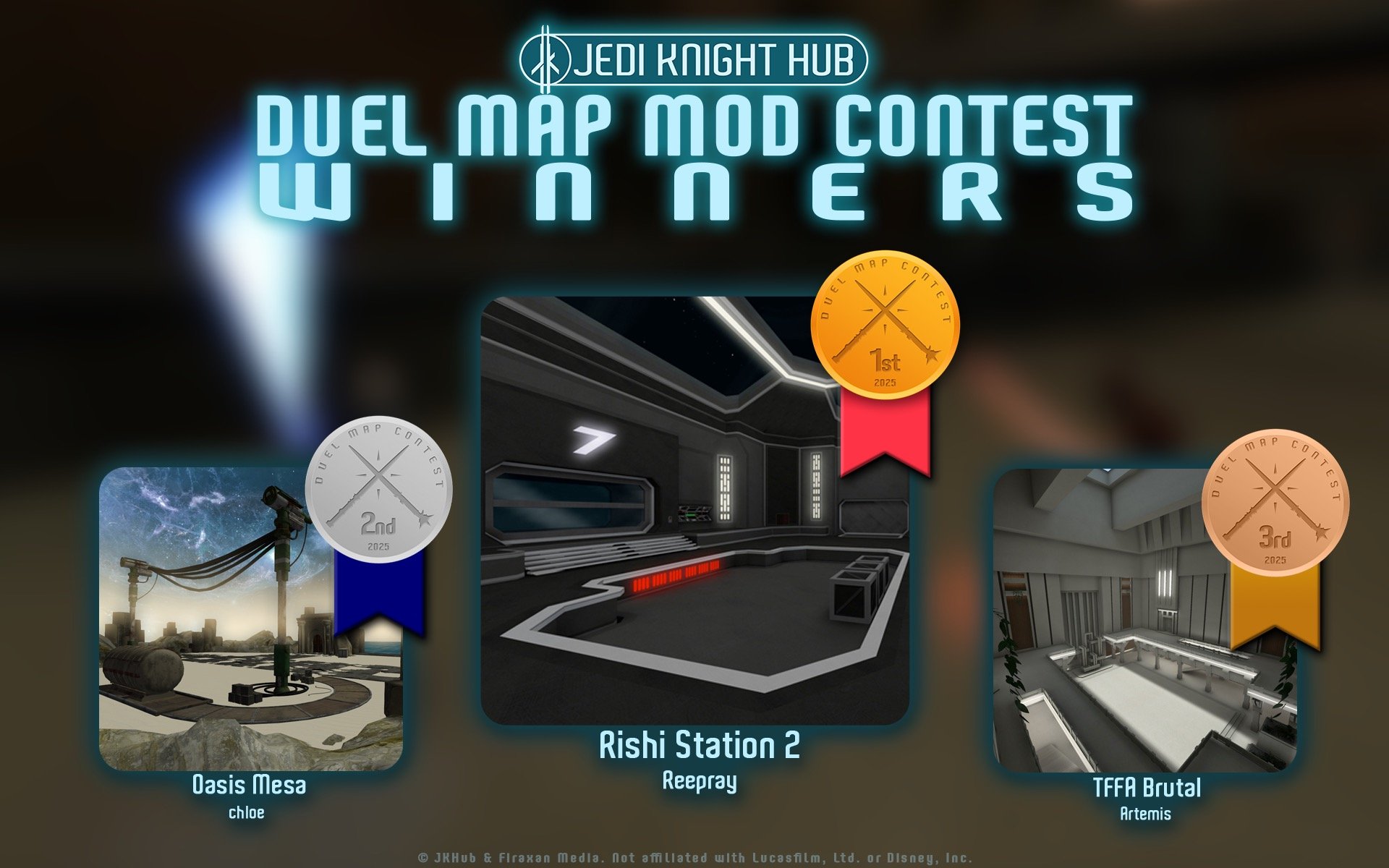
 1st Place Winner Reepray with Rishi Station 2,
1st Place Winner Reepray with Rishi Station 2,  2nd Place Winner chloe with Oasis Mesa, and
2nd Place Winner chloe with Oasis Mesa, and  3rd Place Winner Artemis with TFFA Brutal! Amazing submissions by everyone!
3rd Place Winner Artemis with TFFA Brutal! Amazing submissions by everyone!




![[WIP] Ecumenopolis Jedi Embassy](https://jkhub.org/uploads/monthly_2025_06/1.jpg.b3a365564310335934555654d97bdb2b.jpg)


.thumb.png.053fed0bde4d93770c561af1841c0c3e.png)











































.thumb.jpg.5dcb19c4514c273ccb909b62bb79a3e3.jpg)




